continued.....
Threat Reports and Blogs
Threat Reports and Blogs give you insights into the new Tactics, Techniques, and Procedures used by the attacker. This information gives you an understanding of how other companies handle exploits, what types of malware the industry is seeing, what new techniques are being used to defend and attack, what are the new emerging threats etc.
Find the
Reports and Blogs of well-known security researchers Teams
like Nocturnus, SecureList, Spider Labs, Cisco, Red Canary, Crowdstrike and The DFIR report (my favorite) so on. Try to look for how this can impact your industry or organization. Make it a goal to take away at least one security recommendation you can apply to your organization or job from each threat report you read.
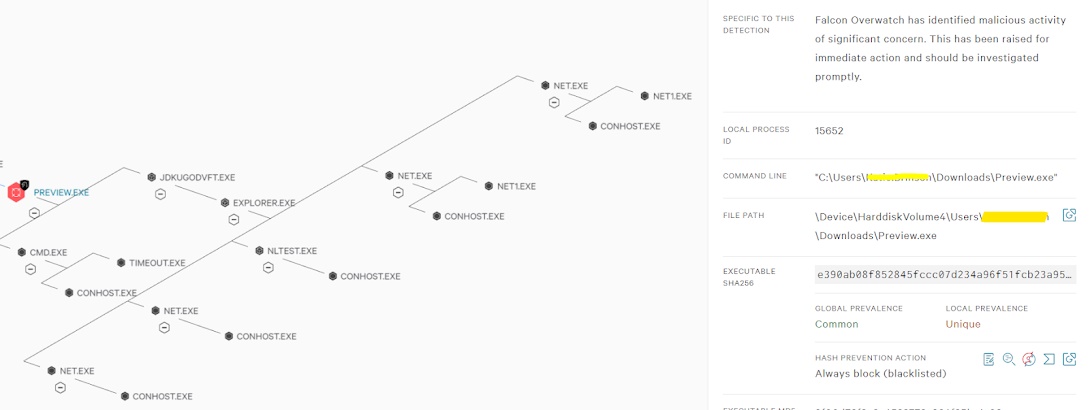
For example, you are reading the latest report from the Red canary and observed the most common techniques used by an attacker are command and scripting interpreter T1059 where Powershell plays a very important role in the windows environment. Usually, PowerShell scripts are obfuscated by an attacker to evade the defense mechanism and bypass the security solutions.  |
| Powershell as a Hypothesis |
The goal is to evading the detection, spawning additional processes, downloading and executing remote code & binaries, gathering information, change system configuration, etc.
There are different methods that can be deployed to prevent such attacks setting up PowerShell execution policy, PowerShell logging, etc. The strings to observe like Invoke-Expression (or variants like iex and .invoke), the DownloadString or DownloadFile methods, or unusual switches like -nop or -noni. Keep an eye on Encoding command switch commands like -e, -ec, -encodecommand, -encoded, -enc, -en, -encod, -enco . Understanding and correlating all the parameters we can build up the logic which is useful to create a new threat hunt hypothesis.
In addition to building your own hypotheses, many well-written threat reports will list their own security recommendations.
Threat Hunting Using MITRE ATT&CK
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. Think of it as an encyclopedic reference that describes TTPs adversaries use, provides suggestions for detection and common mitigations for specific techniques, and profiles APT groups’ known practices, characteristics, and specific attack attributions. ATT&CK also provides an extensive list of software used in attacks (both malware and commercially available and open-source code that can be used legitimately or maliciously). All information captured in ATT&CK comes from publicly available data and reports as well as from the community—threat researchers and security teams in the trenches experiencing or analyzing attacks daily. MITRE ATT&CK also provides a listing of "N" number APTs and the sectors they target. By looking at which APTs commonly attack which industries, you can get a better sense or idea for the kinds of threats that are most prevalent in your environment.
Adversary tactics as per MITRE ATT&CK are categorized as below:
- Reconnaissance: gathering information to plan future adversary operations, i.e., information about the target organization
- Resource Development: establishing resources to support operations, i.e., setting up command and control infrastructure
- Initial Access: trying to get into your network, i.e., spear phishing
- Execution: trying the run malicious code, i.e., running a remote access tool
- Persistence: trying to maintain their foothold, i.e., changing configurations
- Privilege Escalation: trying to gain higher-level permissions, i.e., leveraging a vulnerability to elevate access
- Defense Evasion: trying to avoid being detected, i.e., using trusted processes to hide malware
- Credential Access: stealing accounts names and passwords, i.e., keylogging
- Discovery: trying to figure out your environment, i.e., exploring what they can control
- Lateral Movement: moving through your environment, i.e., using legitimate credentials to pivot through multiple systems
- Collection: gathering data of interest to the adversary goal, i.e., accessing data in cloud storage
- Command and Control: communicating with compromised systems to control them, i.e., mimicking normal web traffic to communicate with a victim network
- Exfiltration: stealing data, i.e., transfer data to cloud account
- Impact: manipulate, interrupt, or destroy systems and data, i.e., encrypting data with ransomware
Within each tactic of the MITRE ATT&CK matrix, there are adversary techniques, which describe the actual activity carried out by the adversary. Some techniques have sub-techniques that explain how an adversary carries out a specific technique in greater detail.
For example, a security team in the healthcare space may identify the group DeepPanda as a relevant threat to their organization. The security team can use this information to create an adversary emulation plan and look for threats in their existing system from this group. MITRE ATT&CK has identified many common techniques used by DeepPanda, including the use of PowerShell scripts to download and execute programs in memory without writing to disk. Threat hunters can use this knowledge to create a hypothesis that there may be PowerShell scripts running on their system that are malicious. From there, they can begin the hunt.
Malware Intelligence
Malware analysis is the process of understanding the behavior and purpose of a suspicious file or URL. The output of the analysis aids in the detection and mitigation of the potential threat. Technical indicators are identified such as file names, hashes, and strings such as IP addresses, domains, and file header data can be used to determine whether that file is malicious. In addition, tools like disassemblers and network analyzers can be used to observe the malware without actually running it in order to collect information on how the malware works. Dynamic malware analysis executes suspected malicious code in a safe environment called a sandbox. This closed system enables security professionals to watch the malware in action without the risk of letting it infect their system or escape into the enterprise network. The dynamic analysis provides threat hunters and incident responders with deeper visibility, allowing them to uncover the true nature of a threat. As a secondary benefit, automated sandboxing eliminates the time it would take to reverse engineer a file to discover the malicious code.
By combining basic and dynamic analysis techniques, the hybrid analysis provides the security team the best of both approaches –primarily because it can detect malicious code that is trying to hide, and then can extract many more indicators of compromise (IOCs & IOAs) by statically and previously unseen code.
If you are able to detect and get a sample of a malware, you can build a hypothesis around its activity. In a lab environment, run malware that has successfully infiltrated your system in the past, or a piece of malware you find interesting. Observe its behavior. Formulate questions based on this behavior.
The dynamic analysis would detect that, and analysts would be alerted to circle back and perform basic static analysis on that memory dump. As a result, more IOCs would be generated and zero-day exploits would be exposed.
Malware analysis can expose behavior and artifacts that threat hunters can use to find a similar activity, such as access to a particular network connection, port, or domain. By searching firewall and proxy logs or SIEM data, teams can use this data to find similar threats.
In addition, tools like mimikatz are commonly used by attackers. By running tools like mimikatz in a lab environment, you can identify behaviors that take place in your environment that signal a common attack. See how the system reacts to mimikatz, then use this information to identify its use in your actual environment.
Malware researchers perform malware analysis to gain an understanding of the latest techniques, exploits, and tools used by adversaries. Using the Malware Analysis uncovers more IOC's which helps to Create a Cyber Threat Hunt Hypothesis.
Advisory Emulation
Adversary emulation is a type of red team engagement that mimics a known threat to an organization by blending in threat intelligence to define what actions and behaviors the attacker use. Adversary Emulation is a form of cybersecurity assessment. During this assessment, assessors replicate a specific threat scenario. Adversary emulation helps organizations focus their security testing to prioritize threats that their defenders may face each day. Successful adversary emulation is a collaborative effort between multiple cybersecurity domains of expertise, particularly red team and cyber threat intelligence (CTI) professionals. CTI professionals work with the security operations center (SOC) and senior leadership to determine what types of threats might target the organization, while red teams work to test and probe defenses. Red teams have the tradecraft and skillset to perform malicious actions to subvert defenses, but that expertise is far more valuable to organizations trying to understand the implications of red team findings on their security posture when it is tied to real-world threat data.
Develop an adversary emulation plan to identify each step an attacker will take. MITRE ATT&CK even provides a listing of TTPs, so you can explore the techniques, tactics, and procedures attackers commonly use. By mapping out each phase of an attack, defenders can more clearly understand the attack process and potential red flags when looking for threats.
There is a five-step process to create an adversary emulation plan, execute the operation, and drive defensive improvements. - Gather threat intel
- Extract techniques
- Analyze & organize
- Develop tools and procedures
- Emulate the adversary
In the complete process, you could determine the new detection logic based on :
- How did the threat group use this technique?
- What are Objective of the APT's
- What tools can we use to replicate these TTPs?
- Reveals the Artifacts and Metadata of an attack.
Once this entire process takes place, the red, blue, and purple teams can work with the CTI team to determine the TTP of an actor along with their IOCs & IOAs, which helps to create a new Hypothesis that defends against real-world behaviors.
Additional Important Factors
- Stop making any assumptions about your environment because it will limit your scope when forming a hypothesis and will create blindspots in your defenses.
- For example, don’t assume that all service processes will run by services.exe. Similarly, do not assume that all processes which are unsigned and unknown (hash) are inherently malicious.
- Find the Right Scope: Define your hypothesis in a specific way that designates a clear-cut scope. Too broad, and the hypothesis may become too strenuous to prove. Too narrow, and it may not be very useful.
Keep in mind that the next step after creating the hypothesis is executing it, followed by testing it to completion. Do not create a hypothesis you cannot execute or resolve.
In the Next blog, we will be discussing Threat hunting methodology, Phases, and Steps involved in Threat Hunting. So stay Tuned...








Comments
Post a Comment