TrickBot Malware Family - A Deep Dive using Falcon Crowdstrike
Use Case
Falcon OverWatch has
identified probable TrickBot malware on host NAOUXXXX. A
renamed copy of Vhd2disk was executed on the host, likely from a successful
phish. This in turn wrote and executed a malicious file, likely TrickBot
malware, and established persistence for it with a registry key.
Introduction
Emotet
Often referred to as a banking trojan or worm. It is a very advanced threat that is updated multiple times a day by the cybercrooks controlling it. Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Additionally, Emotet is a polymorphic banking Trojan that can evade typical signature-based detection. It has several methods for maintaining persistence, including auto-start registry keys and services. It uses modular Dynamic Link Libraries (DLLs) to continuously evolve and update its capabilities.
TrickBot
TrickBot is most commonly installed by the Emotet Trojan, which is spread through phishing emails. Once TrickBot is installed, it will harvest various data, including passwords, files, and cookies, from a compromised computer and will then try spread laterally throughout a network to gather more data.
- When done harvesting data on a network, TrickBot will open a reverse shell to the Ryuk operators.
- The Ryuk Actors will then have access to the infected computer and begin to perform reconnaissance of the network. After gaining administrator credentials, they will deploy the ransomware on the network's devices using PowerShell Empire or PSExec.
- These spam emails contain malicious documents that will install the Emotet trojan on the recipient's computer when opened and macros enabled.
- Historically, once a user became infected with Emotet, the trojan would eventually download and install the TrickBot trojan on the infected computer.
- Similar to Emotet, TrickBot is also referred to as a banking trojan and worm. It does a lot of similar activities to Emotet, for example constantly trying to spread to other computers and updating itself multiple times a day.
Ryuk
Combo : Emotet, TrickBot and Ryuk
- This triple threat campaign initiates with a weaponized Microsoft Office document attached to a phishing campaign. The malicious code attached to the document executes a PowerShell command that attempts to download the Emotet payload. Once it succeeded, Emotet infects and gathers information on the affected machine.
- It also initiates the download and execution of TrickBot Trojan from a remote C2 server that it communicates with.
- When TrickBot executes, it creates an installation folder containing a copy of Ryuk malware, encrypted malicious modules, and their configuration files.
- TrickBot also creates a scheduled task and a service to ensure persistence.
- In addition to stealing information using TrickBot, the attackers check if the target machine is a qualified target. If so, they download the Ryuk ransomware payload and use admin credentials stolen by TrickBot to move laterally in the network and search for assets worth to infect. Once they are found, the main Ryuk payload injects itself into multiple processes and achieves persistence by using the registry.
Anatomy Of Attack
IOC :
Description: Falcon Overwatch has identified malicious activity of significant concern. This has been raised for immediate action and should be investigated promptly. Malicious file execution beneath renamed Vhd2disk executable with persistence and reconnaissance on host.
Host name: NAOUXXXX
File name: Preview.exe
File path: \Device\HarddiskVolume4\Users\Kxxxe.Bxxxn\Downloads\Preview.exe
Command line: "C:\Users\Kxxxe.Bxxxn\Downloads\Preview.exe"
SHA 256: e390ab08f852845fccc07d234a96f51fcb23a95a4fa872a22b48afa0cbb0941e
MD5 Hash data: 9f00d78f2e8e4523773a264f85be1c02
Platform: Windows
IP address: 82.146.37[.]128
User name: BXXXX\Kxxxe.Bxxxn
Detected: Sep. 10, 2020 00:32:42 local time, (2020-09-09 19:02:42 UTC)
Last behavior: Sep. 10, 2020 00:32:42 local time, (2020-09-09 19:02:42 UTC)
AV Detections : 29 / 67 Positives
In this case, We Investigate using (EDR) Falcon Crowdstrike :
CrowdStrike is a leader in cloud-delivered endpoint protection. Leveraging artificial intelligence (AI), the CrowdStrike Falcon® platform offers instant visibility and protection across the enterprise and prevents attacks on endpoints on or off the network. CrowdStrike Falcon deploys in minutes to deliver real-time protection and actionable intelligence from Day One. It seamlessly unifies next-generation AV with best-in-class endpoint detection and response, backed by 24/7 managed hunting. Its cloud infrastructure and single-agent architecture take away complexity and add scalability, manageability, and speed.
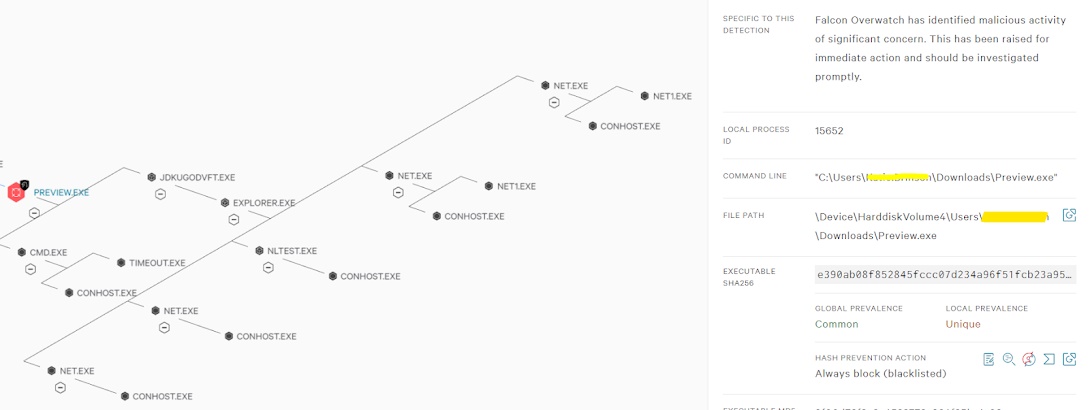
- Explorer.exe
- Chrome.exe
- Preview.exe
- jdkugodvft.exe
- Explorer.exe
- Net.exe
Stages of Cyber Attack :
1) Delivery :
The first stage of the attack starts with a weaponized Microsoft Office document attached to a phishing email. This file contains a malicious, [URL/macro-based code] Url in our case. Once the user opens the document and upon clicking malicious Url will attempts to download the Emotet payload:
Once TrickBot’s main payload is injected into the svchost.exe process, it carries out a series of reconnaissance-related tasks to profile the infected endpoint and the network. This information is crucial, as it determines the course of the attack which will discuss later in the blog.

HASH: e390ab08f852845fccc07d234a96f51fcb23a95a4fa872a22b48afa0cbb0941e
NOTE: Renamed copy of the legitimate Vhd2disk tool, likely a result of a successful phish.
3) Installation :
- Timeout.exe
- Conhost.exe

"jdkugodvft.exe": Probable TrickBot malware written and executed by Vhd2disk

4) Persistence :
4.1) Modifying ASEP Values

Command Line :
4.3) Adding Log-on script in Group Policy.
- GPO scripts can be defined for user and started with GPScript.exe /Logon
- Logon scripts do not show up in Autoruns.exe
- GPscript.exe is responsible for triggering logon scripts when you define them in Group Policy.

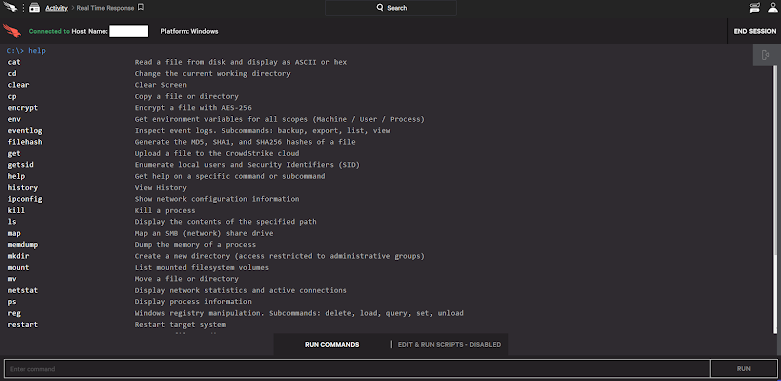
5) Reconnaissance Commands :
executed commands as below:
- net view /all
- net view /all /domain
- nltest /domain_trusts /all_trusts
- net localgroup administrator
- net group /domain admins
- net1 localgroup administrator
- net1 group /domain admins
How to defend against Trickbot
How to defend against Trickbot it is important to ensure a well-organized, multi-layered cybersecurity program is in place within your organization:
- Email and spam filters are critical in the case of Trickbot as this is the initial infection vector.
- Perform regular updates and system hardening as Trickbot uses known Windows SMB exploits for propagation.
- Restrict RDP/terminal services on all levels. Enforce best practice secure configuration:
- limit connections.
- limit devices redirection.
- use network-level authentication and limit authentication types.
- limit RDP groups and RDP user rights assignment authorizations.
- Give employees regular phishing training and conduct regular awareness programs.
- Employ strong password policies and use multi-factor authentication, such as Duo.
- Ensure PowerShell logging and security by limiting and hardening PowerShell usage, logging trusted PowerShell processes and remove remote invoke.
- Ensure updated EDR Solution placed inside the network like Crowdstrike etc.







Comments
Post a Comment