Threat Hunting Maturity Models
Before moving forward in describing the threat hunting maturity models, First, we need to understand what is threat hunting and its basic terminologies. The aim of this article is to learn how organizations can count their organization maturity level and what advancements are required to boost their security posture. The maturity level measures the capabilities of the organizations, which determined to what extent these organizations are capable of hunting and responding to threats.
The threat hunting maturity model is defined by the quantity and quality of data the organization collects from its IT environment. Threat Factors to judge an organization's hunting ability:
- Quality and Quantity of the data they collect for hunting
- Tools provided to access & analyze the data
- Skills of the analyst who actually use the data & tools to find the security incident.
The Hunting Maturity Model, developed by Sqrrl's security architect and hunter David Bianco, describes five levels of organizational hunting capability, ranging from HMM0 (the least capable) to HMM4 (the most). Let's examine each level in detail: 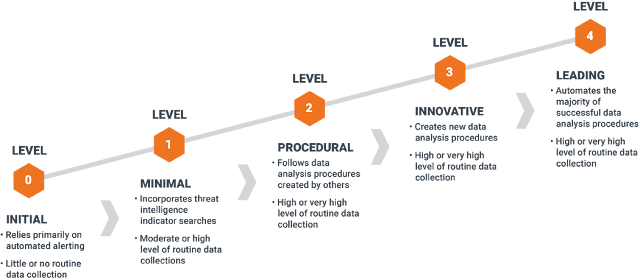 |
| Threat Hunting Maturity Model |
HMM Level 0: Initial
At HMM0, organizations generally use Automated alerting systems like IDS, IPS, NetFlow, SIEM, WAF, Firewall, or antivirus to identify harmful behavior. These companies use open-source services for threat feeds. These indicators mostly correspond to the lower levels of the Pyramid of Pain, trivial data that is unlikely to be reused (domains, hashes, URLs, IP addresses). These organizations likely have little or no visibility in their environments. HMM0 organizations tend to lack actual threat intelligence capability. HMM0 companies do not gather much data from their systems, which greatly restricts their capacity to discover threats proactively. As a result, there is little to no visibility of the environment for these organizations. All this makes HMM0 organizations incapable of threat hunting.
HMM Level 1: Minimal
Like HMM0, organizations still depend heavily on automated alerting to perform their incident response process. But unlike HMM0, where a routine collection of IT data is minimal if at all. organizations have increased their visibility in their environment. These organizations will often rely on the same controls identified in HMM0 for reactive detection.
Organizations at HMM1 will still leverage a SIEM platform for analysis. But, organizations at this maturity will start to expand their SIEM content beyond simple correlations. HMM1 will also start to focus on greater network visibility, especially NetFlow data. This visibility allows organizations to be able to visualize and analyze network metadata. When new threats approach a company’s network, analysts are advised to extract key indicators from threat-related reports and look for historical data to find out if they have been identified in the short run.
Despite its minimal nature, any type of hunting can occur at the HMM1 level due to its search capability. HMM1 organizations will be able to consume more complex indicators. These indicators will likely align with tool-based artifacts found in the NetFlow metadata. These could include:
- User Agent Strings
- Blank or missing fields in HTTP traffic
- Encoded data in the HTTP header
HMM1 organizations are capable of Basic operational hunting. An organization at HMM1 will conduct threat hunting, but only on an ad hoc basis.
HMM Level 2: Procedural
There are several great hunting procedures developed by others and you can find them easily on the internet. These procedures are used to integrate a particular analysis technique with an expected type of input data to identify a single type of malicious activity.
Organizations at
HMM2 in our threat hunting maturity model will have all the same security controls from previous levels. They will also have addressed the lack of visibility at the endpoint level in the environment. HTM2 organizations will deploy tools to log endpoint activity. These tools are likely to be some form of endpoint detection and response (EDR) platform. Other platforms such as extended detection and response (XDR) and endpoint protection platforms (EPP) may also work
Organizations at HMM2 will begin to look for more complex threat detection content for their platforms. This content will look for known malicious behaviours for threats. They will likely rely on free content available from untrusted third parties. HTM2 organizations are also capable of adapting free content for their environment.
Organizations at HMM2 will have to add threat data, information, and intelligence because they failed to generate their own threat intelligence data. This data can be from commercial platforms. This threat intelligence reporting will cover all levels (tactical, operational, and strategic). This threat intelligence may contribute to some limited hunting.
HMM2 organizations will be able to conduct routine threat hunting. Hunting activities are limited to unstructured hunting and more basic analysis methodologies. Organizations at HTM2 will still rely on unstructured (or data-driven) threat hunting. But, these organizations may also try limited hypothesis-based hunting.
HMM Level 3: Innovative
Unlike the HMM2 level, which relies on procedures developed by others, the organizations at level HMM3 create and publish their own data analysis procedures and collect a high or very high level of routine data. With this data, they will have a broad spectrum of choices in where they can pivot and know what to hunt. Organizations at HMM3 in our threat hunting maturity model will have good visibility into their environment at both the network and endpoint levels.
This type of organization may also being to put in place automation platforms like SOAR. These tools will automate manual processes for security analysis and hunting.HMM3 organizations will likely have moved away from traditional SIEM tools. Instead, these organizations are very likely to have data like platforms in place. These platforms rely on hunting and detection content. HMM3 organizations will likely develop their own threat hunting content. This content originates from their knowledge and experience.
Another major difference with HMM3 organizations is their analysis methodologies. Threat intelligence in HMM3 organizations will be organization-specific. This allows organizations to produce targeted intelligence-driven hunts. These hunts will focus on tools, techniques, as well as actors and threats targeting their organization or vertical. Organizations will continue to ingest threat feeds, but will be very selective on the feeds used. These feeds should provide mapping to specific industry frameworks.
Organizations that achieve HMM3 often find that their team consists of only a handful of hunters. As a result, those teams are may experience challenges when resources move on. Large organizations will often be incapable of sustainable, repeatable, and rigorous threat hunting. This is due to time constraints presented by primary hunting activities. Teams won’t have time to focus on tasks such as threat detection content creation and playbook development. HMM3 organizations are able to focus on sustainable threat hunting of high complexity.
Several advanced analysis disciplines are incorporated at this level including machine learning, data analysis, and data visualization. More importantly, HMM3 companies must have highly-skilled hunters who completely understand data analysis techniques and apply them to detect malicious activities.
HMM Level 4: Leading
The
HMM4 level is similar to level 3, but the main difference between them is the aspect of automation. At this level, analysts operationalize any successful hunting process in order to turn it into automated detection.
An organization that has developed to
HMM4 in our threat hunting maturity model has addressed its resource issues. This means that the organization is able to maintain ongoing threat hunting operations.
These organizations are able to focus on secondary tasks such as tool and content development. The results of this development are published to the broader community. HMM1 and HMM2 organizations are likely to consume this content.
Doing so release the analysts from the burden of carrying out the same processes again and again. In this way, they can focus on creating new processes or improving existing ones, which results in a constant enhancement to the detection mechanism as a whole.
Threat Hunting Loop
As we saw above, hunting maturity is based on a number of criteria that determine how effectively
an organization can get through the hunting process. But what is involved in the actual process of
hunting? if the goal of an organization is automated hunting then what could be the steps involved for threat Hunting?
It is important for your team to implement a
formal cyber threat hunting process.
Sqrrl has developed a Threat Hunting Loop consisting of four stages that define an effective hunting approach.
The goal of a hunt team should
be to get through the hunting process as quickly and effectively as possible. The more efficiently you can iterate,
the more you can automate new processes and move on to find new threats.
 |
Sqrrl Threat Hunting Loop
|
There are 4 stages involved in Cyber Threat hunting Loop as follows:
- Create Hypothesis
- Investigate Via Tools and Techniques
- Uncover New Patterns & TTP's
- Inform and Enrich Analytics
A hunt starts with creating a hypothesis, or an educated guess, about some type of activity that might be going on in your IT environment. An example of a hypothesis could be that users who have recently traveled abroad are at elevated risk of being targeted by state-sponsored threat actors, so you might begin your hunt by planning to look for signs of new malware on their laptops or assuming that their accounts are being misused around your network. Hypotheses are typically formulated by analysts based on any number of factors, including friendly and threat intelligence. There are various ways that a hunter might form a hypothesis. Often this involves laying out attack models and the possible tactics a threat might use, determining what would already be covered by automated alerting systems, and then formulating a hunting investigation of what else might be happening.
Hypotheses are investigated via various tools and techniques, including Linked Data Search and visualization. Effective tools will leverage both raw and linked data analysis techniques such as visualization, statistical analysis or machine learning to fuse disparate cybersecurity datasets. Linked Data Analysis is particularly effective at laying out the data necessary to address the hypotheses in an understandable way, and so is a critical component for a hunting platform. Linked data can even add weights and directionality to visualizations, making it easier to search large data sets and use more powerful analytics. Many other complementary techniques exist, including row-oriented techniques such as stack counting and datapoint clustering. Analysts can use these techniques to easily discover new malicious patterns in their data and reconstruct complex attack paths to reveal an attacker’s Tactics, Techniques, and Procedures (TTPs).
Tools and techniques uncover new malicious patterns of behavior and adversary TTPs. This is a critical part of the hunting cycle. An example of this process could be that a previous investigation revealed that a user account has been behaving anomalously, with the account sending an unusually high amount of outbound traffic. After conducting a Linked Data investigation, it is discovered that the user’s account was initially compromised via an exploit targeting a third party service provider of the organization. New hypotheses and analytics are developed to specifically discover other user accounts affiliated with similar third party service providers.
Finally, successful hunts form the basis for informing and enriching automated analytics. Don’t waste your team’s time doing the same hunts over and over. Once you find a technique that works to bring threats to light, automate it so that your team can continue to focus on the next new hunt. Information from these hunts can also be used to improve existing detection mechanisms. For example, you may uncover information that leads to new threat intelligence or indicators of compromise. You might even create some friendly intelligence, that is, information about your own environment and how it is meant to operate, such as network maps, software inventories, lists of authorized web servers, etc. The more you know about your own network, the better you can defend it, so it makes sense to try to record and leverage new findings as you encounter them on your hunts.
The hunting loop is a simple but effective step-by-step process that can radically enhance an organization’s control over its own network defense. As noted above, hunting is most effective when it is used together with other more traditional security systems, complementing the detection efforts and perimeter security that most organizations already have in place.
The above blog covers the Threat Hunting Maturity Models and Threat Hunting Loop/process defined by Sqrrl, Next blog will be more on Hypothesis where insights include how to generate a hypothesis, what is the starting point, hypothesis examples, and multiple ways to create a hypothesis.
Click here to read Part 1 of the Threat hunting series!!!
Stay Tuned...









Comments
Post a Comment