TrickBot Malware Family - A Deep Dive using Falcon Crowdstrike
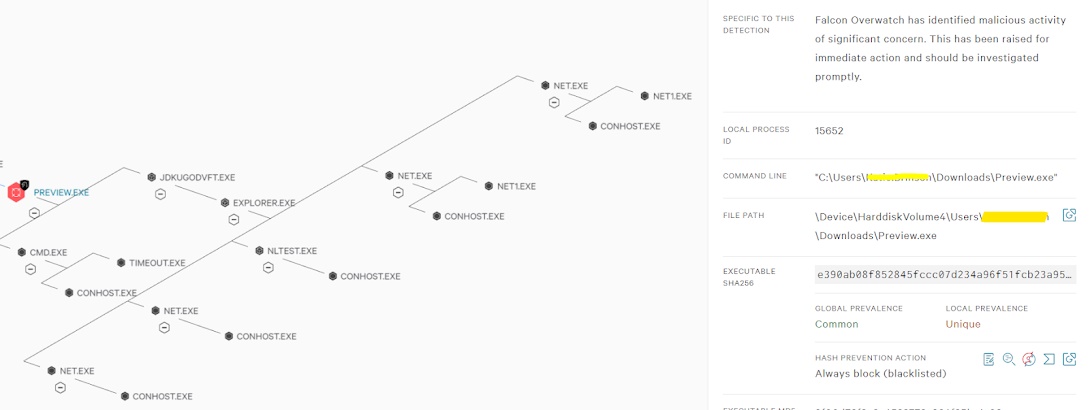
Use Case Falcon OverWatch has identified probable TrickBot malware on host NAOUXXXX. A renamed copy of Vhd2disk was executed on the host, likely from a successful phish. This in turn wrote and executed a malicious file, likely TrickBot malware, and established persistence for it with a registry key. Introduction Emotet Often referred to as a banking trojan or worm. It is a very advanced threat that is updated multiple times a day by the cybercrooks controlling it. Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Additionally, Emotet is a polymorphic banking Trojan that can evade typical signature-based detection. It has several methods for maintaining persistence, including auto-start registry keys and services. It uses modular Dynamic Link Libraries (DLLs) to continuously evolve and update its capabilities. TrickBot TrickBot is most commonly installed by the Emotet Trojan, which is spread through phishing em