RTR using Falcon Crowdstrike
You can also connect to a host from Hosts > Host Management.
Once connected, you will be presented with a list of commands and capabilities available in Real Time Response. With the ability to run commands, executables and scripts, the possibilities are endless. A few examples are listed below.
Falcon has three Real Time Responder roles to grant users access to different sets of commands to run on hosts.
Real Time Responder - Read Only Analyst (RTR Read Only Analyst) - Can run a core set of read-only response commands to perform reconnaissance
Real Time Responder - Active Responder (RTR Active Responder) - Can run all of the commands RTR Read Only Analyst can and more, including the ability to extract files using the
getcommand, run commands that modify the state of the remote host, and run certain custom scriptsReal Time Responder - Administrator (RTR Administrator) - Can do everything RTR Active Responder can do, plus create custom scripts, upload files to hosts using the put command, and directly run executables using the
runcommand.
RUNNING COMMANDS
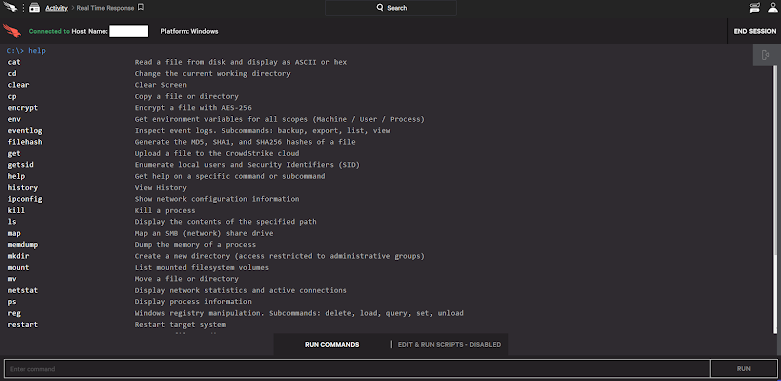
On the host you are connected to, you can run commands from the list in the Run Commands tab of the Real Time Response window. Run the help command for a list of all available commands.
C:\> help
RUNNING CUSTOM SCRIPTS
On the Run Commands tab, you have two options to populate the command field to run a custom script:
Expand the session details panel from the right to see available custom scripts under Saved scripts. Click the name of any script to populate the command field with
“runscript -CloudFile=”<Script_Name>” -CommandLine=””
Run the
runscriptcommand with one of the following flags:CloudFile: Enter the name of an existing custom script already saved in the CrowdStrike cloud directly into the command line
Raw: Enter the script content directly into the command line. (RTR Administrator only). Enclose the entire script contents in triple backticks.
HostPath: Enter the file path of an existing custom script stored locally on the remote host (RTR Administrator only)
TESTING A CUSTOM SCRIPT
Test out potential response scripts before saving them. You can run any PowerShell command from the Edit & Run Scripts tab of a response session without saving. When you are ready to add it to your list of custom scripts, click Save.
CREATING A NEW CUSTOM SCRIPT
You can reach the "Create a custom script" dialog either from the Response Scripts & Files page or from within a Real Time Response session.
From the Response Scripts & Files page, click Create a script.
From a Real Time Response session, go to the Edit & Run Scripts tab and click Save.







Comments
Post a Comment