Threat Hunting Basics - Part 5
Threat Hunting Methodology
A threat hunter is a security analyst who uses manual or machine-assisted techniques to detect, isolate, and neutralize APTs that are not detected by automated security tools. Threat hunters assume that adversaries are already in the system, and they initiate an investigation to find unusual behavior that may indicate the presence of malicious activity. Four Methods involved in the hunting methodology are as follows:
Intel Based or Unstructured Hunting
The Intel-based hunting approach involves the reactive hunt technique associated with new threats. These IOCs become a trigger point for the threat hunter to uncover the malicious activity going on.
You can check out the previous blog which shows how Threat intelligence can be useful for the threat hunting approach.
Behavior-based or Structured Hunting
The most proactive threat-hunting technique is an investigation using indicators of attack or Indicators of behavior. This technique commonly aligns with threat frameworks such as MITRE ATT&CK.
Here are the actions that are most often involved in the process:
- Use IOAs and TTPs to identify threat actors.
- The hunter assesses the domain, environment, and attack behaviors to create a hypothesis that aligns with MITRE.
- After identifying a behavior, the threat hunter attempts to locate patterns by monitoring activities. The goal is locating, identifying, and then isolating the threat.
Hypothesis Based Hunting
This threat hunting technique involves testing three types of hypotheses:
- Analytics-driven: makes use of machine learning (ML) and user and entity behavior analytics (UEBA) to develop aggregated risk scores and formulate hypotheses
- Intelligence-driven: includes malware analysis, vulnerability scans, and intelligence reports and feeds
- Situational-awareness driven: enterprise risk assessments and crown jewel analysis (the identification of the digital assets that are critical to the company) Attackers commonly target specific high-value or high-risk assets or privileged users such as IT administrators, domain controllers, development managers, and C-level Executives. Threat hunting helps identify these high-priority targets and conduct focused searches for relevant threats.
Hypotheses can also be targeted not at predicting the future steps of the attackers but at understanding patterns, dependencies, and so on. In other words, seeing the whole picture.
Custom or Hybrid Hunting
The hybrid threat hunting technique combines all of the above methods, allowing security analysts to customize the hunt. For example, the hunt can be customized using data about geopolitical issues. You can also use a hypothesis as the trigger, and leverage IoAs and IoCs.
Threat Hunting Steps
A cyber threat hunt is composed of steps or processes designed for an efficient, successful hunt. These steps include:
Step 1: Hypothesis
Threat hunts begin with a hypothesis or a statement about the hunter’s ideas of what threats might be in the environment and how to go about finding them. A hypothesis can include a suspected attacker's tactics, techniques, and procedures (TTPs). Threat hunters use threat intelligence, environmental knowledge, and their own experience and creativity to build a logical path to detection.
Step 2: Collect and Process Intelligence and Data
Hunting for threats requires quality intelligence and data. A plan for collecting, centralizing, and processing data is required. Security Information and Event Management (SIEM) software can provide insight and a track record of activities in an enterprise’s IT environment.
Step 3: Trigger
A hypothesis can act as a trigger when advanced detection tools point threat hunters to initiate an investigation of a particular system or specific area of a network.
Step 4: Investigation
Investigative technology can hunt or search deep into potentially malicious anomalies in a system or network, ultimately determined to be benign or confirmed as malicious.
Step 5: Response/Resolution
Data gathered from confirmed malicious activity can be entered into automated security technology to respond to resolve, and mitigate threats. Actions can include removing malware files, restoring altered or deleted files to their original state, updating firewall /IPS rules, deploying security patches, and changing system configurations – all the while better understanding what occurred and how to improve your security against similar future attacks.
Phases of Threat Hunting
One of the core realities of threat hunting is that we need access to data to verify integrity. I cannot validate whether a system is still in a trusted state unless I have access to data that identifies that system’s current operational state. If I’m hunting on the network, visibility is a non-issue.
With host-based threat hunting, data access can be hit or miss. It can be extremely difficult to identify if you are collecting logs from all of your devices. In fact, you can be pretty certain you are not, given the number of BYOD, IoT, and forgotten hardware devices (like printers) that end up on the typical network. Clearly, if I’m not getting logs from a device, I have no way of evaluating that device’s integrity.
Further, modern malware tries really hard to cover its tracks. So even if I am collecting log entries from a host, the malware that now owns that system may be altering logs in an effort to go undetected.
So think of network-based threat hunting as the great equalizer. While an attacker may be able to hide the processes they are running on a system, they cannot hide their packets on the wire. The best they can hope for is to get lost in the rest of the traffic on the network.
This does not mean host logs have no value. When we threat hunt the network, we are trying to determine if each session is trustworthy or a potential threat. Sometimes the network does not have all the answers. For example, I may see that one of my internal systems is holding open a TLS-protected session with an external host 24 hours a day. For me personally, I would be 75% certain that this is due to a compromise or an internal employee breaching policy. With this evidence in hand, I would now turn to host logs to identify what process is responsible for that session, and why it is running on the system. At this point, however, I’ve switched into more of a forensic analysis mode than threat hunting.
Hunting for Network threats
Network threat hunting actively checks every network connection of every IP on the network. By using outgoing network traffic to identify anomalous, possibly malicious connections based on connection frequency, connection duration, cumulative connection duration, and connections to multiple subdomains over DNS, the network defender can identify C2 channels. This helps prioritize connections for further investigation and incident response.
Few examples to start with the network hunt as below but not limited to:
- Web requests with an unusual HTTP protocol version.
- User agents that are not commonly used in your organization. Do not blindly trust user agent information, however, since this can easily be crafted.
- Excessive size or a repeating pattern in the size of HTTP requests.
- Persistent connections (beacons) to HTTP servers on the internet, even outside regular office hours.
- Repeated requests for the same web resource, possibly on different domains, with a similar parameter format.
- Requests to a social network site outside regular office hours. Attackers can encode their commands -textually on a page on a social network and present them like legitimate messages.
- Alerts on DNS queries for domains that have only recently been registered.
- DNS responses that have a very low time to live (TTL).
- Repeated requests for domains belonging to a dynamic DNS service or requests for URL shortener domains.
- Statistics for DNS queries on the full qualified domain name (FQDN), focusing on the second-level domain. Be aware that this can also generate lots of false positives due to content delivery networks (CDNs).
- Netflow statistics for workstations that establish a high number of connections or flows. and Firewall log entries indicating outbound IRC or P2P traffic.
- Communications to potential suspicious ports
- Hunt for ICMP packets between 2 IP address that is consecutive for a long duration
- Outbound connection to a rare country IP
Hunting for Host/Endpoint threats
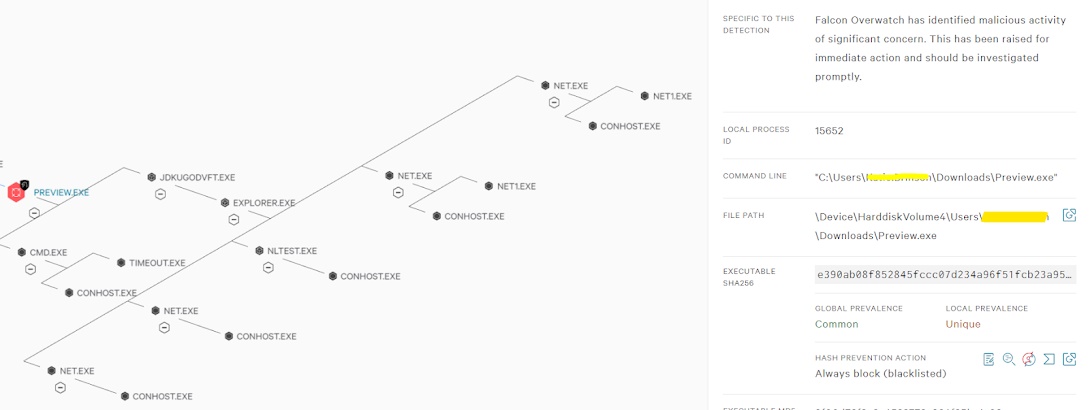
Examine endpoints for malware involvement in the registry, file system, and elsewhere. Host-based threat-hunting can be achieved by observing the suspicious or abnormal behavior/activity of the processes, binaries, registries, malicious scripts, loaded drivers, removable media, system configuration, authentication events, fileless attacks, local firewall rules, etc.
Few examples to start with the Host-based hunt as below but not limited to:
- Potential Maldoc Execution Chain
- PowerShell Encoded Command Execution
- Unusual Process Execution Path - Recycle Bin
- LSASS Memory Dumping using WerFault.exe
- User Activity from Clearing Event Logs
- User Activity from Stopping Windows Defensive Services
- Suspicious scheduled tasks created
- suspicious service installed
- Reg.exe called from Command Shell
- Process injection from the unusual process
- Msiexec process communicating with a malicious domain
- Regsvr32 scriptlet execution by communicating with malicious domain and executed using scrobj.dll
- ASEP registry modification by the unsigned binary
- Unusual Parent-child relationship in the process.
I hope you found the above blog informative, The next blog will be more on skills needed to be a good Threat hunter.
Stay Tuned....








Comments
Post a Comment