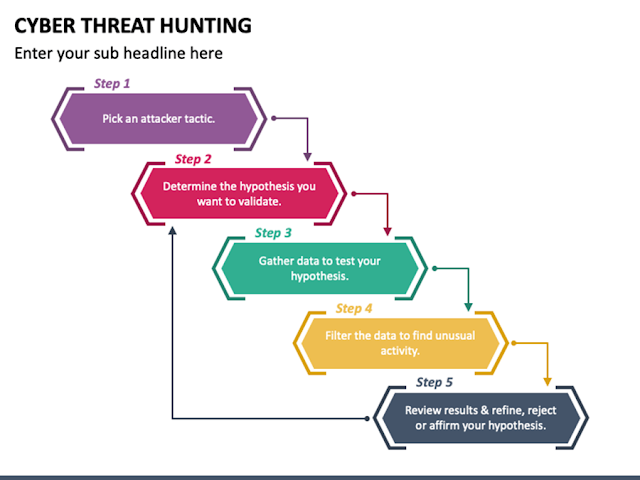
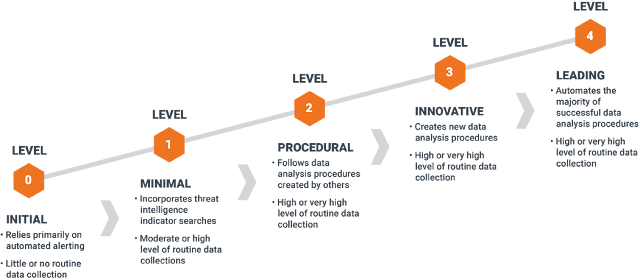
Threat Hunting Basics - Part 4

continued..... Threat Reports and Blogs Threat Reports and Blogs give you insights into the new Tactics, Techniques, and Procedures used by the attacker. This information gives you an understanding of how other companies handle exploits, what types of malware the industry is seeing, what new techniques are being used to defend and attack, what are the new emerging threats etc. Find the Reports and Blogs of well-known security researchers Teams like Nocturnus , SecureList , Spider Labs , Cisco , Red Canary , Crowdstrike and The DFIR report (my favorite) so on. Try to look for how this can impact your industry or organization. Make it a goal to take away at least one security recommendation you can apply to your organization or job from each threat report you read. For example, you are reading the latest report from the Red canary and observed the most common techniques used by an attacker are command and scripting interpreter T1059 where Powershell plays a very import