Threat Hunting Basics - Part 3
All about Threat Hunting "HYPOTHESIS"
A threat hunt hypothesis is a proposed explanation made on the basis of limited evidence from a security environment, and this proposed explanation is then used as a starting point for further investigation. Threat hunting is primarily hypothesis driven. This means that quite often each hunt will begin with a series of questions or theories. Generalized questions could include, “If I were to attack this environment, how would I do it? What would I attempt to gain access to? What would be my targets?” These types of questions then lead to hypotheses that can be tested. They may begin looking for odd services, unusual network connections, unusual parent-child processes, abnormal behaviors, maximum numbers of registry or file modifications, or anything that seems unusual for this device or environment. In many cases, the hunt may return no results, but that does not mean that this particular theory was incorrect. These theories should not be seen as rigid because they can be further expanded upon and refined based on evidence gained during the view of collected data.
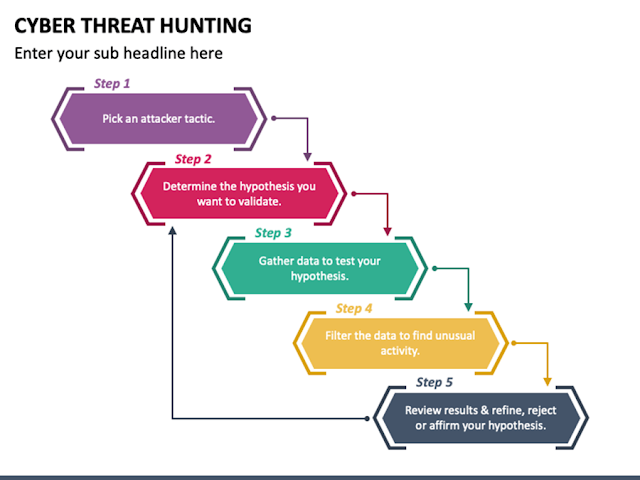 |
| Hypothesis Life cycle |
As shown in the above diagram, how the flow of hypothesis will bring out the successful hunt. It begins with choosing the tactics and techniques, gathering the data, findings the anomaly, and executing the hunt.
- External Intelligence
- Internal Intelligence
- Power of Social media
- Google knows Everything
- Threat Reports and Blogs
- Threat hunting using Mitre Att&ck
- Malware Intelligence
- Advisory Emulation
- Additional Important Factors
External Intelligence
- Unusual traffic going in and out of the network
- Unknown files, applications, and processes in the system
- Suspicious activity in administrator or privileged accounts
- Anomalous spikes of requests and read volume in company files
- Network traffic that traverses in unusually used ports
- Unusual Domain Name Servers (DNS) requests and registry configuration
- Unauthorized settings changes, including mobile device profile
- Large amounts of compressed files or data bundles in incorrect or unexplained locations
Internal Intelligence
Internal intelligence and insider threats are the ones which are originated within the target organization. It typically involves a current or former employee or business associate who has access to sensitive information or privileged accounts within the network of an organization, and who misuses this access. Traditional security measures are merely focused on external threats and are not always capable of identifying an internal threats emerging from inside the organization.
There is much to learn from a previous incident in your organization. An attack may leave traces that give clues as to where there are holes in an organization’s defenses. Traces of an attack can give threat hunters an idea of where similar threats may be, as well as how they function.
Based on behaviors and actions observed in a previous attack, ask yourself how these behaviors could impact your current environment. Did you patch the issue properly? If any users are particularly careless with security or caused an incident, have their habits changed?
Trackable insider threat indicators or Internal intelligence includes :
- Unusual logins
- Use or repeated attempted use of unauthorized applications
- An increase in escalated privileges
- Excessive downloading of data
- Unusual employee behavior
- Remotely accessing the network while on vacation, while out sick, or outside of typical working hours
- Working outside of typical working hours without authorization
- A notable enthusiasm for shifts where they’ll have minimum supervision such as overtime, weekend, or unusual work schedules
- An increase in copying materials, particularly if the materials are proprietary or classified and the copying appears to be unnecessary
- Having an unusually keen interest in matters outside of the scope of their duties
- Visits to websites that may indicate low productivity, disengagement, job discontent, and potential legal liabilities (e.g. hate sites, pornography, excessive unproductive browsing)
- Uploading huge data to the cloud.
The above are a few internal Intelligence instances that we can collect and make a story from the same which leads to a new Hypothesis. There are multiple solutions available to detect insider threat that gives lots of internal intelligence such as UEBA (User Entity Behavior Analytics), SIEM, and SOAR (Security Orchestration, Automation, and Response), etc.
Power of Social Media
Social media channels are a good and at times essential and simple way to remain informed. Whether this comes in the form of a threat report, a single tweet on a specific behavior or an IOC, or some other means, many social media channels have useful information.
Follow the Hashtags like #infosec, #threathunting, #dfir, #malware, #cybersecurity, #phishing, #ransomeware, #bugbounty, #databreach etc
Find the channels of well-known security researchers on Twitter: @cyb3rops , @samwcyo , @briankrebs , @schneierblog , @gcluley , @thegrugq , @shirastweet , @chrispcritters , @troyhunt , @mikko , @brianhonan , @hydeNS33k , @beakerLinkedin: Bill Brenner, Maya Schirmann, Steve Morgan, Yotam Gutman, Bob Carver, Robert Herjavec, Chuck Brooks, Bob Carver, Paul Asadoorian, Meisam Eslahi, Laurent CrahayYoutube: John Hammond, Hackersploit, dist67, BlackPearl, 13Cubed, Security Now, IppSec, Gerald Auger, SANS cyber Defense, Linode, Null Byte, STOK, InsiderPHD, LiveOverflow, BlueTeamVillage What makes social media different from other mediums is the immediacy of knowledge. The second a new variant is discovered, you can know about it through the power of social media. It’s a way of keeping up-to-date with the latest in the community, which can be invaluable and timely.
Without social media, it would be much more difficult to reach such a wide audience in such a short amount of time. So, keep your eye on the trending news, hacks, breaches, and exploits, which help to develop the detection logic and are useful to create your hypothesis. Google Knows Everything!!! Google knows everything, so of course, it knows about threat hunting, data breaches, exploits, vulnerabilities, POCs, malware, Reverse engineering, and the list go on. Google dork queries are ways to search Google with advanced search operators to pinpoint the information you are looking to find when threat hunting. It is considered a passive attack method but can be used to find usernames, passwords, email lists, sensitive information, and even some website vulnerabilities.
This is the power of Google dorks: this particular query finds PDFs located on unipune.ac.in with the string “sensitive but unclassified” in them. They are an easy way to sift through the massive supply of data Google has available, and are particularly useful for threat hunters.
For example, if you identified specific unknown commands in your environment, you could use Google dorks to search the entirety of GitHub. By searching GitHub for strings matching the commands, you could potentially find a malicious tool used to attack your system based on those commands. With this data, you can learn more about the threat.
Google Dorking, also known as Google hacking, is the method capable of returning information difficult to locate through simple search queries by providing a search string that uses advanced search operators. Primarily, ethical hackers use this method to query the search engine and find crucial information. This Google hacking cheat sheet will help you carry out Google Dorking commands and access hidden information. We can filter the Google database by the commands like but not limited to Intext. Allintext, Filetype, Intitle, inurl, Site, ext, etc For example as below,
Command: allinurl:log4jvulnerabilities
Follow the Hashtags like #infosec, #threathunting, #dfir, #malware, #cybersecurity, #phishing, #ransomeware, #bugbounty, #databreach etc
Find the channels of well-known security researchers on
Without social media, it would be much more difficult to reach such a wide audience in such a short amount of time. So, keep your eye on the trending news, hacks, breaches, and exploits, which help to develop the detection logic and are useful to create your hypothesis.
Google knows everything, so of course, it knows about threat hunting, data breaches, exploits, vulnerabilities, POCs, malware, Reverse engineering, and the list go on. Google dork queries are ways to search Google with advanced search operators to pinpoint the information you are looking to find when threat hunting. It is considered a passive attack method but can be used to find usernames, passwords, email lists, sensitive information, and even some website vulnerabilities.
This is the power of Google dorks: this particular query finds PDFs located on unipune.ac.in with the string “sensitive but unclassified” in them. They are an easy way to sift through the massive supply of data Google has available, and are particularly useful for threat hunters.
For example, if you identified specific unknown commands in your environment, you could use Google dorks to search the entirety of GitHub. By searching GitHub for strings matching the commands, you could potentially find a malicious tool used to attack your system based on those commands. With this data, you can learn more about the threat.
Google Dorking, also known as Google hacking, is the method capable of returning information difficult to locate through simple search queries by providing a search string that uses advanced search operators. Primarily, ethical hackers use this method to query the search engine and find crucial information. This Google hacking cheat sheet will help you carry out Google Dorking commands and access hidden information. We can filter the Google database by the commands like but not limited to Intext. Allintext, Filetype, Intitle, inurl, Site, ext, etc For example as below,








Comments
Post a Comment