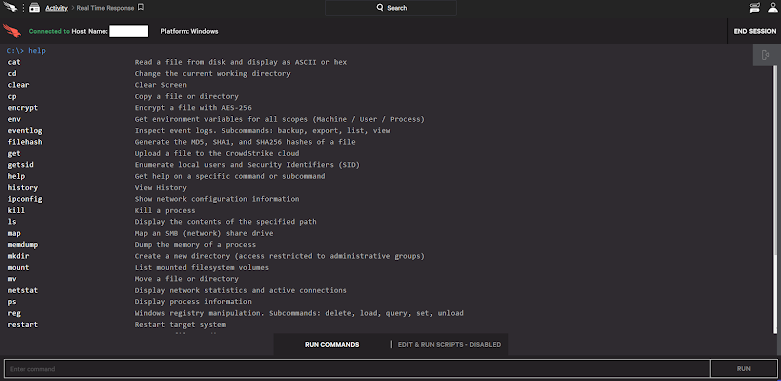
Top Commands Mostly Used By System Administrator.
Top Commands Mostly Used By System Administrator.
1) IPconfig
Simply entering ipconfig
at the command line will return basic addressing information for your system,
including the adapter name, IP address, subnet mask, and default gateway.
2) IPconfig /all
Shows all networking
information for the system, including host name, node type, adapter names,
MAC addresses, DHCP lease information, etc.
3) Ping
Ping command to verify that a host can be reached over
the network. This command is useful for diagnosing host and network
connectivity problems. The device sends a series of ICMP echo (ping)
requests to a specified host and receives ICMP echo responses.
4) Ping "Website-name"
This above command used to find the IP address associated with The Specific Website. eg: 10.24.126.25 is the IP address for Website Intranet.indusind.com
5) Tracert "IP address"
Tracert command-line utility that you can use to trace the path that an Internet Protocol (IP) packet takes to its destination.
6) Netstat
The netstat Command is used to display very detailed information about how your computer is communicating with other computers or network devices. Specifically, the netstat command can show details about individual network connections, overall and protocol-specific networking statistics, and much more, all of which could help troubleshoot certain kinds of networking issues.
7) Nbtstat -a "Remote-Host"
The nbtstat command displays information about the NetBIOS
over TCP (NBT) connection for the Filer. It displays the
IP address associated with the interfaces, the broadcast
IP mask, the IP addresses of the WINS servers in use, and
information about the registered NetBIOS names for the
filer.
8) Nslookup
nslookup command is used to querying the DNS ( Domain Name System) to option host name (domain name) or IP address. Nslookup command is used to resolve DNS. Nslookup command used to troubleshoot forward and reverse DNS lookup.
9) Route Print
A route (path) to a specific Network ID in the inter-network.
10) Net config "[Server\Workstation]"
net config displays a list of configurable services.
server : Displays and allows you to make changes to the settings for the Server service while the service is running.
workstation: Displays and allows you to make changes to the settings for the Workstation service while the service is running.
11) Net User
Net User Command shows the Accounts Present in the System.
12) Net User "Account" *
This command is used to change the Password for Specific Account. Before Executing it you must open CMD with Administrative Privileges.
13) DriverQuery
This Command Used to Display the List of Drivers installed on the System with Given Name, Date and Time.
14) TaskList
This command used to Show List of Processes along with Their Name, Process ID and Memory Usage.
15) Taskkill /pid "1234"
We can kill a process from GUI using Task manager. If you want to do the same from command line., then taskkill is the command you are looking for. This command has got options to kill a task/process either by using the process id or by the image file name.
16) Wmic Bios Get command
Short for WMI console, wmic is a command line command to query WMI entries, we can use this command to get the system details like serialnumber, version, status etc as shown in image below.
Please Share If you like
Thank You :-)
1) IPconfig
 |
| IPCONFIG |
2) IPconfig /all
 |
| IPCONFIG/ALL |
3) Ping
 |
| PING |
4) Ping "Website-name"
 |
| PING TO WEBSITE |
This above command used to find the IP address associated with The Specific Website. eg: 10.24.126.25 is the IP address for Website Intranet.indusind.com
5) Tracert "IP address"
 |
| TRACE COMMAND |
Tracert command-line utility that you can use to trace the path that an Internet Protocol (IP) packet takes to its destination.
6) Netstat
 |
| NETWORK STATISTICS |
The netstat Command is used to display very detailed information about how your computer is communicating with other computers or network devices. Specifically, the netstat command can show details about individual network connections, overall and protocol-specific networking statistics, and much more, all of which could help troubleshoot certain kinds of networking issues.
7) Nbtstat -a "Remote-Host"
 |
| NBT COMMAND |
8) Nslookup
 |
| NSLOOKUP |
nslookup command is used to querying the DNS ( Domain Name System) to option host name (domain name) or IP address. Nslookup command is used to resolve DNS. Nslookup command used to troubleshoot forward and reverse DNS lookup.
9) Route Print
 |
| ROUTE PRINT |
A route (path) to a specific Network ID in the inter-network.
10) Net config "[Server\Workstation]"
 |
| NETCONFIG |
net config displays a list of configurable services.
server : Displays and allows you to make changes to the settings for the Server service while the service is running.
workstation: Displays and allows you to make changes to the settings for the Workstation service while the service is running.
11) Net User
 |
| NETUSER |
Net User Command shows the Accounts Present in the System.
12) Net User "Account" *
 |
| NETUSER |
This command is used to change the Password for Specific Account. Before Executing it you must open CMD with Administrative Privileges.
13) DriverQuery
 |
| DRIVERQUERY |
This Command Used to Display the List of Drivers installed on the System with Given Name, Date and Time.
14) TaskList
 |
| TASKLIST |
This command used to Show List of Processes along with Their Name, Process ID and Memory Usage.
15) Taskkill /pid "1234"
 |
| TASKILL |
We can kill a process from GUI using Task manager. If you want to do the same from command line., then taskkill is the command you are looking for. This command has got options to kill a task/process either by using the process id or by the image file name.
16) Wmic Bios Get command
 |
| wmic command |
Short for WMI console, wmic is a command line command to query WMI entries, we can use this command to get the system details like serialnumber, version, status etc as shown in image below.
Please Share If you like
Thank You :-)






Hello Mr.Author,
ReplyDeleteThank you well for sharing the big blast to us... It's extraordinarily helpful and informative.
Please keep blogging new updates.
Reliable dedicated hosting
Businesses are, in today’s information economy, wide open to internal and external threats. Each possible entry and exit are potential points of vulnerabilities. Serious Security Alarm systems Werribee
ReplyDeletepersonal Computer
ReplyDelete