Firewall is software or hardware that prevents unauthorized access to or from network. All data entering and leaving the internet must pass through firewall and Blocked/Allow as per policies are set.
There are different types of firewalls which is used and implements as per the requirements of the organisation. Software firewall is free and inbuilt in windows based operating system.
However, we have to pay for hardware firewall which also more preferable and strongly recommended for one of the best Defensive Mechanisms.
Types :
- Packet Filtering Firewall
- Application Gateway firewall
- Circuit Level Gateway firewall
- Statefull packet Inspection Firewall
- Next-Generation Firewall
- Cloud Firewall
Packet Filtering Firewall :
Packet Filtering firewall filters the traffic packet by packet by simply looking the header file of IP packet.
Packet Filtering has two parts :
- Selection Criteria: It defines Conditions or Pattern Matching of packet used for Decision making.
- Action Filed: It depends upon whether IP packet meets the Selection Criteria and upon that Packet will be Allow or Block.
Filtering of packets is done on various parameters like Source IP, Destination IP, Source port, Destination Port and various other fields in packet Header.
Application Gateway firewall :
Application Gateway is a Application program which runs on Firewall systems between two networks. Application Gateway is also called as Proxy Servers and behaves like intermediate between Source & Destination Hosts.
Proxy servers examines and filters individually packets rather than simply forwarding them blindly.
Application gateway verifies the contents inside the packets rather than filtering on basis of source IP, Destination IP, source port and Destination Port.
For outbound packets Proxy server replaces source IP address by its own IP address, which is called as NAT (network address translation).
Circuit Level Gateway Firewall :
Its is intermediate solution between Packet filter and Application gateway. Runs at transport Layer hence Acts as Proxy for any application.
It setups two TCP segments and relays tcp segments from one network to other sometime called as PIPE proxy.
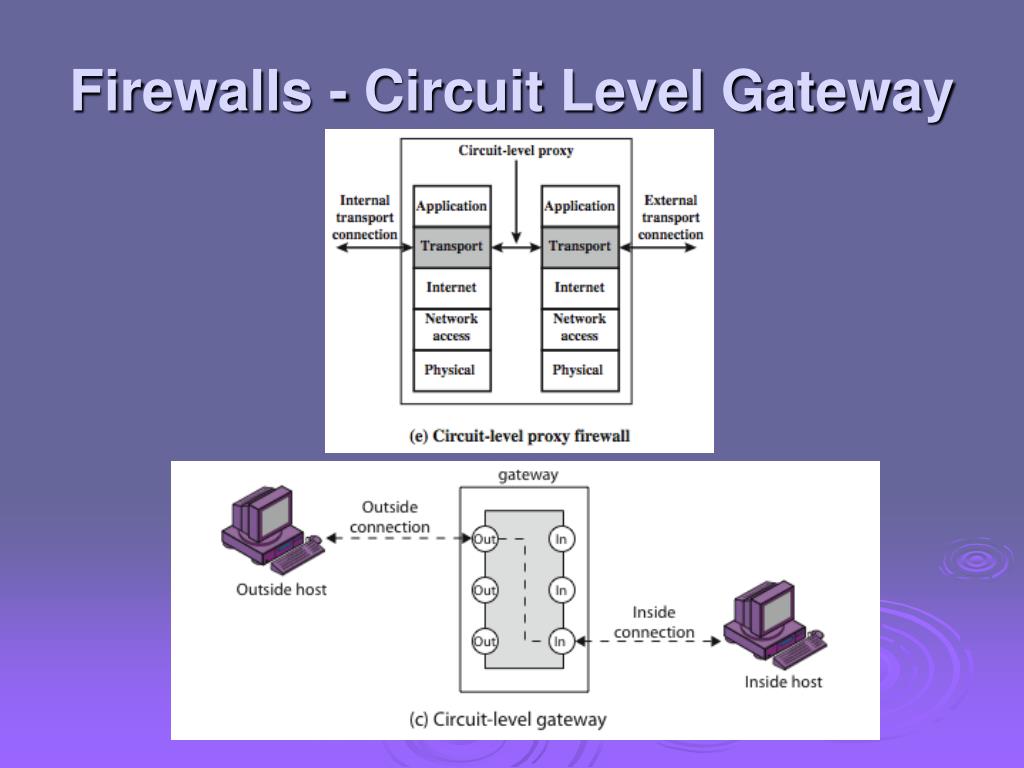
Monitors TCP handshaking between local and remote host to determine whether the session being initiated by legitimate user or not.
Socks proxy is typical implementation of Circuit Level Gateway Firewall.
StateFul Packet Inspection :
In Stateful packet Inspection makes decision not only on IP addresses and Port number but also on ACK, SYN , Sequence numbers and other data contains in Header field of IP packet.
Tracks the Sessions of each sessions and dynamically open and close ports as specific session requires.
Maintains a Active table, also called as Connection table which maintains all in progress sessions and compares incoming packets to this table to assist in control decisions.
If Packet reaches its Final destinations then it builds or updates its connection table for the conversation.
Reduces the chances that a Packet will be Spoofed.
Next-Generation Firewall (NGFW) :
A next generation firewall (NGFW) is, as Gartner defines it, a “deep-packet inspection firewall that moves beyond port/protocol inspection and blocking to add application-level inspection, intrusion prevention, and bringing intelligence from outside the firewall.”
Next generation firewalls are a more advanced version of the traditional firewall, and they offer the same benefits. Like regular firewalls, NGFW use both static and dynamic packet filtering and VPN support to ensure that all connections between the network, internet, and firewall are valid and secure. Both firewall types should also be able to translate network and port addresses in order to map IPs.
There are also fundamental differences between the traditional firewall and next generation firewalls. The most obvious difference between the two is an NGFW ability to filter packets based on applications.
These firewalls have extensive control and visibility of applications that it is able to identify using analysis and signature matching. They can use whitelists or a signature-based IPS to distinguish between safe applications and unwanted ones, which are then identified using SSL decryption.
Cloud Firewall :
Cloud Firewalls are software-based, cloud deployed network devices, built to stop or mitigate unwanted access to private networks. As a new technology, they are designed for modern business needs, and sit within online application environments.
Many Advantages of Cloud Firewall which includes Scalability, Availability, Extensibility, Migration Security, Secure Access Parity, Identity Protection and Performance Management.
Next Generation Firewalls are cloud-based services intended to deploy within a virtual data center. They protect an organization’s own servers in a platform-as-a-service (PaaS) or infrastructure-as-a-service (IaaS) model. The firewall application exists on a virtual server and secures incoming and outgoing traffic between cloud based applications.
One potential downside of any cloud based service (especially in regards to cloud firewalls) is that users have to rely on the availability of their FaaS provider. Any level of downtime for a cloud firewall service provider can open up multiple organizations to security breaches, with no immediate safety available. Because of this, many service providers maintain security teams in charge of responding to major issues.
Which Firewall Architecture is Right for Your Company?
The particular firewalls that you will want to use will depend on the capabilities of your network, relevant compliance requirements for your industry, and the resources you have in place to manage these firewalls.









Comments
Post a Comment